Discover Pi Network’s security-first approach in 2024, focusing on user safety and account protection. Learn about the security measures implemented, including KYC verification and blockchain integrity, ensuring a reliable and secure environment for all users.
Ensuring Safe Blockchain Use
Blockchain technology has rapidly transformed digital interactions, providing a decentralized and transparent framework for transactions, data sharing, and record-keeping. However, as adoption increases, the security risks associated with blockchain systems become more pronounced. Ensuring trust and reliability within this ecosystem demands a comprehensive approach to security. Pi Network, a blockchain-based platform, has set itself apart by prioritizing a security-first approach, addressing vulnerabilities, and innovating solutions to protect its users.
A secure blockchain platform is essential for fostering trust among users. Whether it’s safeguarding financial transactions or ensuring personal data privacy, robust security measures are integral to blockchain’s widespread acceptance. Pi Network understands this necessity and has incorporated advanced security protocols that not only enhance safety but also promote inclusivity.
This article delves into Pi Network’s multi-faceted security strategy, exploring how its innovations and proactive measures safeguard its users and the blockchain ecosystem. As a platform that has democratized cryptocurrency access through mobile mining, Pi Network serves as a model of how security and innovation can coexist.
In the sections below, we will explore blockchain security fundamentals, examine Pi Network’s unique features, and dive deep into its security protocols. From the technical intricacies of its consensus mechanism to the role of its community in security enhancements, every aspect of its strategy is analyzed in detail.
The focus is not just on what Pi Network has achieved but also on how it plans to navigate future challenges. With millions of active users globally, maintaining trust and security has become even more crucial. Let’s begin by understanding the foundational concepts of blockchain security.
Understanding Blockchain Security
Blockchain security is the backbone of any decentralized network. It encompasses a series of protocols, cryptographic techniques, and operational guidelines that ensure the system’s integrity, confidentiality, and availability. This section breaks down these aspects and their relevance to Pi Network.
-
Defining Blockchain Security
Blockchain security involves protecting the system against unauthorized access, data breaches, and fraud. This is achieved using cryptographic techniques, secure protocols, and robust consensus mechanisms. Every transaction added to the blockchain is validated and encrypted, ensuring its authenticity. -
Why Blockchain Security Is Critical
Unlike centralized systems, blockchains operate without a single governing entity, making them inherently resistant to certain types of attacks. However, this decentralization also introduces risks, such as the possibility of a 51% attack where a group gains control of the majority of the network’s computational power. -
Challenges in Maintaining Security
Blockchain systems face multiple challenges, including phishing attacks targeting private keys, vulnerabilities in smart contracts, and potential breaches in nodes. These challenges necessitate continuous vigilance and innovation in security measures. -
The Role of Cryptography
Cryptography ensures data integrity and confidentiality by encrypting information during transmission and storage. This prevents unauthorized parties from accessing or altering data. Pi Network employs advanced cryptographic techniques to secure its ecosystem. -
Consensus Mechanisms and Security
Consensus algorithms, such as Proof of Work (PoW) and Proof of Stake (PoS), are essential to validate transactions. Each has its vulnerabilities, which platforms like Pi Network aim to address through alternative protocols. -
How Security Builds Trust
The success of any blockchain platform hinges on user trust. When users feel confident that their data and transactions are secure, they are more likely to participate actively in the ecosystem. -
Pi Network’s Solution
Pi Network tackles these challenges head-on by implementing a multi-layered security approach that protects both its infrastructure and its users. -
A Model for Blockchain Security
By understanding and addressing these challenges, Pi Network serves as a case study in how a blockchain can balance innovation with security.
Pi Network: An Overview
Pi Network has emerged as one of the most popular blockchain platforms, largely due to its unique approach to making cryptocurrency mining accessible and secure for everyday users. Its emphasis on simplicity and safety sets it apart.
-
Origins and Vision
Pi Network was founded by a team of Stanford graduates in 2019. Their vision was to create a cryptocurrency platform that anyone with a smartphone could access, democratizing the world of blockchain. -
User-Friendly Approach
The platform’s intuitive interface allows users to mine cryptocurrency with minimal effort, requiring no prior technical knowledge. This accessibility has been a key driver of its growth. -
The Role of Mobile Mining
Unlike traditional mining methods, which demand high computational power, Pi Network introduced mobile mining. This feature is designed to be energy-efficient and user-friendly, making it accessible to millions of users globally. -
Community-Centric Growth
The platform’s focus on building a strong community has been instrumental in its success. Users are encouraged to contribute, engage, and share feedback, fostering a sense of ownership and trust. -
Popularity and Adoption
With millions of users worldwide, Pi Network is one of the fastest-growing blockchain platforms. This rapid adoption underscores the need for robust security measures to maintain trust and reliability. -
Security as a Cornerstone
From the outset, Pi Network has prioritized security to ensure its community’s safety. This includes advanced encryption, decentralized identity management, and continuous monitoring of its systems. -
Bridging the Gap Between Users and Blockchain
Pi Network’s approach makes blockchain accessible to those who may have previously been excluded due to technical or financial barriers. -
Innovation Meets Security
Through its innovative solutions and unwavering commitment to security, Pi Network exemplifies how blockchain platforms can cater to a diverse global audience.
The Security-First Approach: Key Pillars
Pi Network’s security-first strategy is built upon foundational principles that ensure the protection of its users and the integrity of its blockchain.
-
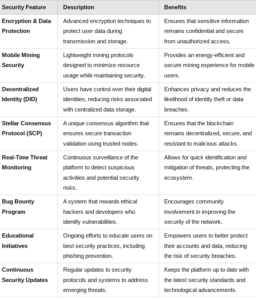
Encryption and Data Protection
Advanced encryption techniques are employed to secure user data at every stage, from transmission to storage. This ensures that sensitive information remains confidential. -
Multi-Layered Security Architecture
A comprehensive, multi-tiered approach addresses threats at every level, from network infrastructure to endpoint devices. Each layer works in tandem to create a robust defense. -
Decentralized Identity (DID)
DID technology empowers users by giving them control over their digital identities, significantly reducing the risks associated with centralized data breaches. -
Continuous Threat Monitoring
Pi Network conducts ongoing security audits and real-time monitoring to identify and mitigate potential vulnerabilities before they can be exploited. -
Community Involvement
The Pi community plays a vital role in strengthening security. By crowdsourcing insights and encouraging user feedback, the platform benefits from a collective effort to identify risks. -
Regular Security Updates
The platform’s developers consistently release updates to improve security protocols, adapting to emerging threats and technological advancements. -
Education and Awareness
Users are educated about best practices for maintaining their security, such as safeguarding their private keys and avoiding phishing attempts. -
A Foundation for Growth
These pillars not only protect users but also create a stable environment for the platform’s continued growth and innovation.
Consensus Algorithm: A Safer Alternative
Consensus algorithms play a critical role in ensuring the security and efficiency of blockchain platforms. Pi Network’s choice of the Stellar Consensus Protocol (SCP) demonstrates its commitment to balancing security, scalability, and accessibility.
-
What Is a Consensus Algorithm?
A consensus algorithm ensures agreement among nodes in a decentralized network about the validity of transactions. It is the backbone of blockchain operations, maintaining the integrity of the ledger. -
SCP: An Overview
Pi Network leverages the Stellar Consensus Protocol, which relies on federated Byzantine agreement (FBA) to achieve consensus. Unlike Proof of Work (PoW) or Proof of Stake (PoS), SCP emphasizes trust within the network. -
Advantages of SCP
SCP’s trust-based model allows for faster transaction validation with minimal computational overhead. It is more energy-efficient than PoW and avoids the centralization risks associated with PoS. -
Security Features of SCP
By incorporating a system of trusted nodes, SCP minimizes the risk of malicious actors gaining control of the network. The protocol is resilient to attacks and ensures transaction finality. -
Comparing SCP to Other Algorithms
Traditional PoW requires significant energy consumption and poses environmental concerns, while PoS can favor wealthier participants. SCP offers a more sustainable and equitable alternative. -
How SCP Benefits Pi Network
For Pi Network, SCP ensures that the platform remains accessible and efficient while maintaining high security standards. Its lightweight nature aligns with the mobile mining model. -
Challenges of SCP
Although SCP is robust, it requires careful selection of trusted nodes. Pi Network mitigates this challenge by leveraging its strong and diverse community. -
Setting a Standard in Consensus
Pi Network’s use of SCP exemplifies how an innovative consensus mechanism can provide both security and inclusivity, setting a standard for the blockchain industry.
Protecting User Privacy
User privacy is a cornerstone of Pi Network’s security framework. With increasing concerns about data breaches and misuse, Pi Network has implemented rigorous measures to safeguard its users’ personal information.
-
Privacy Challenges in Blockchain
While blockchain inherently offers some level of anonymity, it is not immune to privacy concerns. Transaction data, though pseudonymous, can be traced back to users under certain circumstances. -
Encryption as a Primary Defense
Pi Network employs advanced encryption techniques to protect user data at all times. This ensures that sensitive information, including transaction details and identity verification, remains secure. -
Decentralized Identity (DID) Implementation
DID gives users control over their identities, allowing them to manage their personal data without relying on centralized authorities. This reduces vulnerabilities associated with centralized data storage. -
Transparency in Data Usage
Users are informed about how their data is collected, stored, and used. Pi Network’s transparent approach builds trust by aligning with global privacy regulations like GDPR. -
Data Minimization Practices
The platform collects only the information necessary for its operations, reducing the risk of exposing users to potential breaches. -
Real-Time Monitoring for Privacy Breaches
A robust monitoring system identifies and addresses potential privacy risks in real time, ensuring continuous protection of user data. -
Educational Initiatives on Privacy
Pi Network educates its users on best practices for maintaining privacy, such as recognizing phishing attempts and safeguarding private keys. -
An Industry-Leading Approach
Through its privacy-centric measures, Pi Network sets an example for other blockchain platforms, proving that privacy and functionality can coexist.
Securing Mobile Mining
Pi Network’s mobile mining feature is a revolutionary concept that brings cryptocurrency mining to the fingertips of users worldwide. However, it also introduces unique security challenges that the platform has successfully addressed.
-
The Concept of Mobile Mining
Unlike traditional mining methods, which require expensive hardware and high energy consumption, mobile mining leverages the computational power of smartphones without draining resources. -
Challenges in Mobile Mining Security
Smartphones are vulnerable to malware, phishing attacks, and unauthorized access. These threats can compromise the mining process and user data. -
Lightweight Mining Protocols
Pi Network employs a lightweight mining protocol that minimizes resource usage and reduces exposure to potential attacks. This ensures that users can mine safely without impacting device performance. -
Authentication and Access Control
Secure login methods, such as two-factor authentication (2FA), protect user accounts and prevent unauthorized access to mining operations. -
Real-Time Threat Detection
The platform monitors for suspicious activity in real time, identifying and neutralizing potential threats before they can cause harm. -
Secure Wallet Integration
Pi Network’s wallet is designed to be secure, ensuring that mined cryptocurrency is protected from unauthorized transfers or hacking attempts. -
Balancing Security and Usability
The platform achieves a delicate balance between robust security measures and a seamless user experience, making mining accessible to all. -
A New Standard in Mining
By addressing the unique challenges of mobile mining, Pi Network has set a benchmark for how blockchain platforms can innovate while maintaining high security standards.
Community-Driven Security Enhancements
The Pi Network community is an integral part of its security strategy. By involving users in identifying and addressing vulnerabilities, the platform has created a collaborative approach to blockchain security.
-
The Role of Community in Security
Community members serve as an additional layer of defense, reporting suspicious activities and providing insights into potential threats. -
Bug Bounty Programs
Pi Network encourages ethical hackers and developers to identify vulnerabilities through bug bounty programs, rewarding them for their contributions. -
Crowdsourcing Security Solutions
By leveraging the collective knowledge of its global community, Pi Network gains innovative ideas for enhancing its security framework. -
Educational Initiatives
The platform educates its community on recognizing and reporting threats, empowering users to take an active role in their security. -
Feedback Loops for Continuous Improvement
User feedback is incorporated into updates and new features, ensuring that the platform evolves to meet emerging security needs. -
Trust-Building Through Transparency
Pi Network fosters trust by being transparent about its security measures and involving the community in its decision-making processes. -
Examples of Community Contributions
Several key security features, such as enhanced wallet protection and phishing detection tools, have been developed based on community input. -
A Collaborative Model for Security
Pi Network demonstrates how involving the community can create a more secure and resilient blockchain ecosystem.
Future Plans for Enhanced Security
As technology evolves, so do the threats to blockchain security. Pi Network is committed to staying ahead by continuously innovating and adapting its security measures.
-
AI-Driven Threat Detection
The platform plans to implement artificial intelligence (AI) to detect and mitigate threats in real time, enhancing its proactive defense capabilities. -
Advanced Cryptographic Techniques
Future updates will include the integration of cutting-edge cryptographic methods to further protect user data and transactions. -
Partnerships with Cybersecurity Experts
Collaborations with leading cybersecurity firms will ensure access to the latest technologies and industry best practices. -
Regular Security Audits
Independent audits will be conducted to identify vulnerabilities and validate the effectiveness of security protocols. -
Integration of Quantum-Resistant Algorithms
As quantum computing advances, Pi Network plans to adopt quantum-resistant encryption methods to future-proof its ecosystem. -
Enhanced Community Engagement
The platform will continue to involve its community in security initiatives, encouraging greater participation and feedback. -
Global Compliance Standards
Adherence to evolving global regulations will ensure that Pi Network remains a trusted and compliant platform. -
Setting the Benchmark for Blockchain Security
These initiatives highlight Pi Network’s commitment to staying at the forefront of blockchain security, setting a benchmark for others to follow.
FAQs
| Question | Answer |
|---|---|
| What is Pi Network’s security-first approach? | It focuses on protecting user data, ensuring privacy, and employing advanced security measures. |
| How does Pi Network ensure user data privacy? | By using encryption, transparent data usage policies, and complying with global regulations. |
| Why is Pi’s consensus algorithm considered secure? | Its Stellar Consensus Protocol prevents malicious control through trusted nodes. |
| Is mobile mining on Pi Network safe? | Yes, Pi Network employs lightweight algorithms and real-time monitoring to secure mobile mining. |
| How can the community contribute to Pi Network’s security? | By reporting vulnerabilities and sharing insights to improve the platform’s resilience. |
| What sets Pi Network apart from other blockchains in terms of safety? | Its multi-layered security, decentralized identity, and community-driven enhancements. |
| What future security enhancements are planned for Pi Network? | AI-driven threat detection, advanced encryption, and collaborations with cybersecurity experts. |
learn more about Pi Network by visiting the official website: minepi.com.